2021.02.23
How to Protect Yourself from Targeted Attack Emails? The Importance of Information Security Education
For companies and organizations to conduct their operations with peace of mind, information security measures are essential.
Companies hold not only information related to their own employees' personal data but also various information about clients and contractors. If this information is leaked improperly, the company will undoubtedly lose trust and suffer significant damage.
Implementing information security measures such as antivirus software, establishing internal rules, and conducting information security training is a challenge that all companies should address to prevent information leaks.

Table of Contents
1. Various Information Security Risks Surrounding Companies
2. Increasing Damage from "Targeted Attacks"
3. The Tactics of Targeted Attacks Are Becoming More Sophisticated! The Belief That Only Large Companies Are Targeted Is a Misconception
4. Targeted Attack Emails Cannot Be Blocked by Security Software!
5. Cultivating Personal Security Awareness Without Over-Relying on Systems and Software
6. E-Learning Materials Available for Information Security Measures
1. Various information security risks surrounding companies
The starting point of information security measures is to understand what kind of "risks" exist. In the course of business, we consider how much risk there is of leaking confidential information.
Risks include "threats" and "vulnerabilities." A threat is a factor that causes a risk. There are human-made threats due to human actions and environmental threats such as disasters.
| Human-made Threats | Intentional | Viruses, theft, eavesdropping, unauthorized access, data tampering, etc. |
|---|---|---|
| Accidental | Careless mistakes such as loss of media or documents, incorrect addresses, and information leaks from conversations, etc. | |
| Environmental Threats | Fire, earthquake, lightning, flood, etc. | |
A vulnerability is a weakness that can be exploited by threats. It refers to security holes such as insufficient antivirus protection, software bugs, or unlocked buildings.
The more vulnerabilities there are, the higher the likelihood of being targeted by malicious attackers and having confidential information stolen.
2. Increasing Damage from Targeted Attacks
When it comes to malicious cyber attacks, in the past, they were mainly perpetrated by thrill-seekers targeting a large number of unspecified individuals. However, recently, attacks aimed at specific organizations or individuals for financial gain have become more prevalent.
These attacks targeting "specific organizations or individuals" are referred to as "targeted attacks."
Among targeted attacks, one of the most common is email-based attacks.
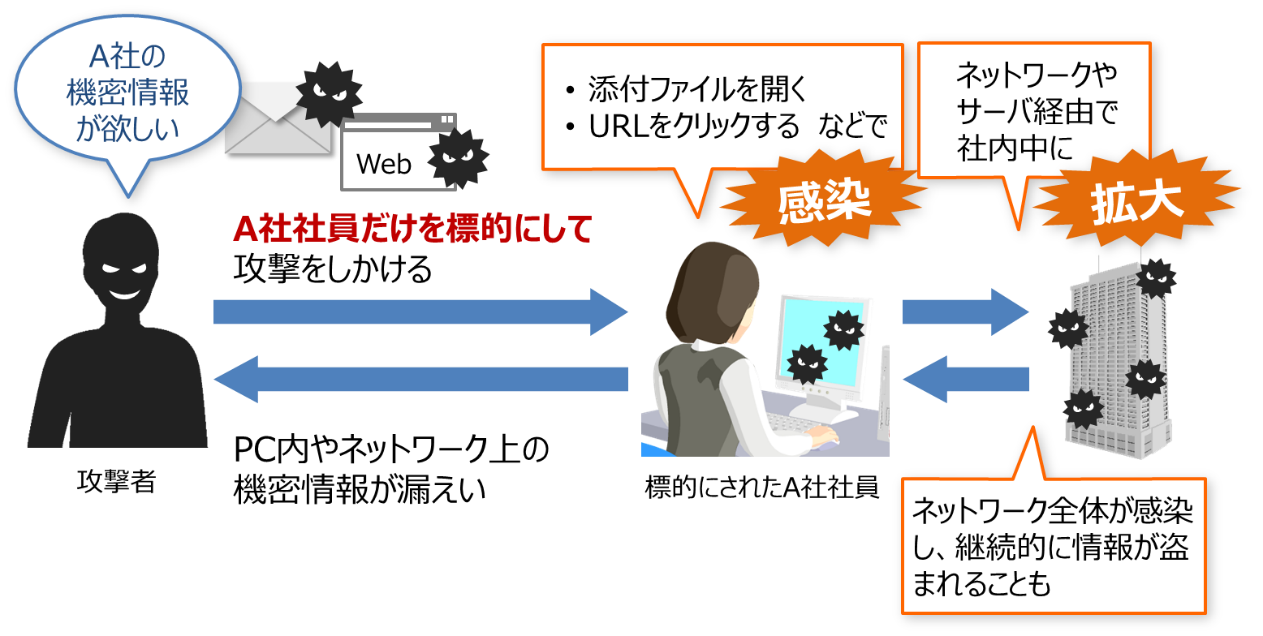
For example, an attacker targeting Company A's confidential information sends a disguised email to an employee of Company A that is "likely to be accidentally opened," infecting the employee's PC with a virus. From the infected PC, the virus spreads through the internal network, stealing confidential information on PCs and networks or destroying systems.
These attacks often continue for long periods, and it is not uncommon for information to be stolen without the victim realizing it.
According to the "Top 10 Information Security Threats" announced annually by IPA (Information-technology Promotion Agency, Japan), targeted attacks have maintained the top position in the "Threats to Organizations" ranking for five consecutive years since 2016. Prior to 2015, there was no distinction between "organizations" and "individuals," so it has been ranked first since the investigation into threats to organizations began. This indicates how prevalent these attacks are in terms of the number of incidents.
| Rank | Threats in the Organization | Last Year's Ranking |
|---|---|---|
| 1st place | The theft of confidential information through targeted attacks | 1st place |
| 2nd place | Information leakage due to internal misconduct | 5th place |
| 3rd place | Financial damage due to business email fraud | 2nd place |
| 4th place | Attacks Exploiting Weaknesses in the Supply Chain | 4th place |
| 5th place | Damage from Ransomware | 3rd place |
| 6th place | Business interruption due to unexpected IT infrastructure failure | 16th place |
| 7th place | Information leakage due to negligence (rules are followed) | 10th |
| 8th place | The theft of personal information from online services | 7th place |
| 9th | Unauthorized Use of IoT Devices | 8th place |
| 10th | Service interruption due to denial-of-service attacks | 6th place |
Source: https://www.ipa.go.jp/security/vuln/10threats2020.html
In November 2020, a major Japanese gaming company experienced an incident where personal information was leaked due to a targeted attack, and a ransom was demanded. It seems that the company was infected with ransomware (an attack that demands a ransom in exchange for stolen information), potentially leading to the leakage of approximately 350,000 pieces of personal information.
3. Targeted attack methods are becoming increasingly sophisticated! The belief that only large corporations are targeted is a misconception.
The methods of targeted attacks are indeed sophisticated. They meticulously research the companies they target, considering factors such as "what kind of subject line would make it easier to open the email" before launching their attacks. They may investigate employees' social media and sometimes even delve into internal relationships.
The email sender and attachments are disguised in such a way that they cannot be easily identified at first glance.
Targeted attacks are often thought to be aimed only at large corporations and that they do not concern individuals, but this is a misconception. Regardless of the size of the company, the department one belongs to, or their position, anyone can be a target.
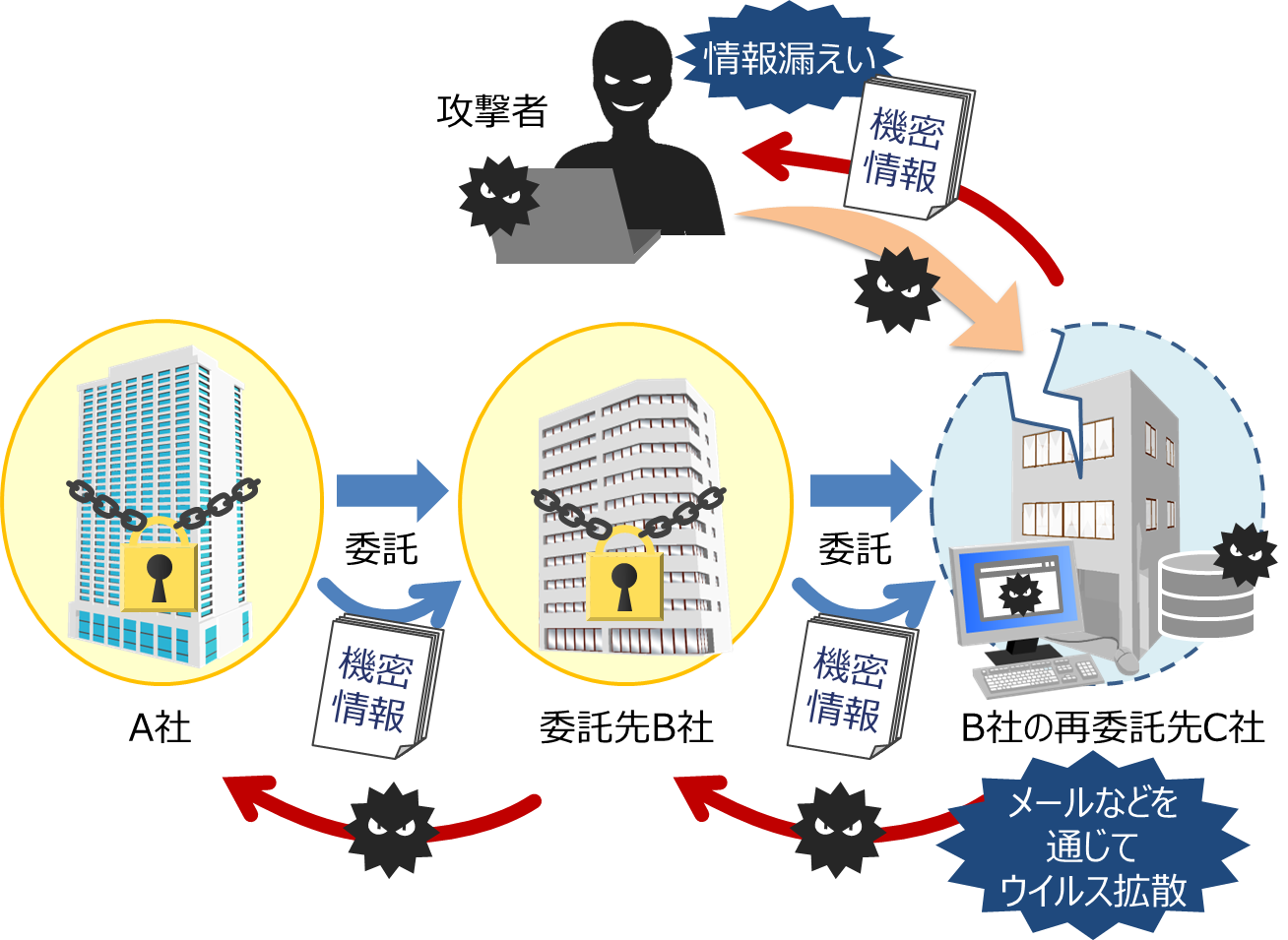
For example, attackers targeting Company A will set traps for anyone even slightly related, such as Company B, which is contracted by Company A, Company C, which is subcontracted, Company D, a business partner, and Company E, which manages servers. If even one person gets infected with a virus, they can spread the infection from there and ultimately reach Company A's confidential information.
4. Targeted attack emails cannot be blocked by security software!
If it is an obvious spam email or nuisance email, such as an unnatural email written only in English, it can be blocked by security software. Some companies may also block suspicious emails before they reach individual mailers.
However, the frightening aspect of targeted attack emails is that they disguise themselves as "very ordinary business emails" in both title and content. There is no software that treats emails with titles like "Request for Quotation" or "Delivery of Minutes" as spam. As a result, emails with viruses attached can reach individual mailers.
If it cannot be mechanically verified, the only option is to determine whether the email is real or fake by human inspection.
・Is the email address correct? Is a free email address being used?
・Is there anything strange in the body text?
・Is the attachment not disguised?
Employees need to develop the ability to notice subtle differences that are different from regular business emails.
5. Cultivate personal security awareness without overly relying on systems and software
The implementation of systems and software for information security measures, such as antivirus software, is certainly necessary. However, information security measures are not something that guarantees absolute safety just by installing this security software. Attackers' methods are becoming increasingly sophisticated, and there are more attacks that software cannot prevent.
It is crucial to abandon the idea that "we are always protected and safe" and for each employee to acquire the correct knowledge of information security measures and conduct their daily tasks with caution. Let's cultivate individual security awareness through information security education.
6. E-learning materials for information security measures
The e-Learning Manuscript Easy Arrangement Series "Fundamentals of Information Security Measures in Corporations: 2020 Case Studies" provided by Human Science is a course that can be used for employee information security training as one of the information security measures. It introduces three threats: "Targeted Attacks," "Supply Chain Attacks," and "Ransomware".
Since it is in PowerPoint format, you can freely edit it to add your company's policies, examples, or even a message from the president.
In addition to the three threats, we also offer a course titled "Fundamentals of Information Security Measures in the Workplace" where you can learn basic knowledge.
If you are struggling with information security measures, please consider it!
e-Learning Manuscript Easy Arrangement Series
"Fundamentals of Information Security Measures in Corporations: 2020 Case Studies"
"Fundamentals of Information Security Measures in Corporations"

Author:
Sayoko Shirochika
Education Solutions Department Production Group
Writer / Consultant
Since joining the company, consistently engaged in e-learning production.
In addition to overseeing the entire project as a director, also responsible for writing scenarios specialized in e-learning.
Currently, leveraging past production experience, also serves in instructional design, scenario writing, and consulting related to e-learning.
Contact Information:
Phone Number: 03-5321-3111
hsweb_inquiry@science.co.jp