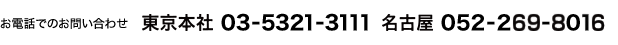2025.03.05
What is ransomware? An explanation of the attack process, infection routes, and measures to take!

One day, if the company's system suddenly stops and a message appears on the PC screen saying, 'Pay the ransom if you want to restore the data'...
This is not a fictional world. Such troubles caused by "ransomware" are actually occurring in many companies. This time, we will explain the mechanism of ransomware, the process of attacks, the infection routes, and the measures to take to prevent infection. Let's acquire the correct knowledge to prepare for any eventuality.
1. What is ransomware?
●What is Ransomware
Ransomware is a type of cyber attack that has been rapidly increasing in recent years. It encrypts stored files and data, taking them as "hostages," and demands a ransom or money in exchange for restoring them.
●Recent Trends in Ransomware
(1) Recognized as the Most Serious Cyber Threat
According to the "Top 10 Information Security Threats 2024" published by the Independent Administrative Institution Information-Technology Promotion Agency (IPA), ransomware has ranked first as "the greatest threat to organizations" for the 9th time in a row over 9 years. This reflects the severity of the damage caused by ransomware.
(2) High Level of Damage Reports
The number of ransomware incidents remains at a high level. Given that various organizations, regardless of their size or industry, are experiencing damage, all companies face risks.
(3) Increase in Targeted Attacks Aimed at Specific Organizations
In recent years, in addition to traditional indiscriminate attacks, there has been a growing trend of "targeted attacks" aimed at specific companies and industries. Attackers research the organization's information in advance and exploit weaknesses to infect, putting companies with insufficient countermeasures at greater risk.
Ransomware is a particularly concerning threat among cyber threats due to the scale of damage and the diversification of attack methods. To prevent infection, it is essential to review your company's security measures once again and prepare for potential damage.
2. Ransomware Attack Process and Infection Pathways
This chapter explains the main attack processes and infection routes of ransomware. Understanding how infections occur and how attacks progress can lead to more effective countermeasures.
Main Routes of Infection
There are three main infection routes for ransomware.

1. Intrusion into the Internal Network
Attackers infiltrate the internal network by exploiting vulnerabilities in VPNs and Remote Desktop Protocols (RDP). There are also many cases where unauthorized access or existing malware is used to gain entry.
* Abbreviation for "Remote Desktop Protocol," a type of communication protocol used to enable remote desktop access.
2. External Attacks via Email
The main source is phishing emails, which can infect by clicking on malicious links or opening attachments.
3. External Attacks via Websites
Simply accessing a website with embedded malware can lead to infection. A typical attack method is the "drive-by download attack."
Main Attack Process
(1) Intrusion
The attacker infiltrates the target system through the above .
(2) Expansion of Internal Activities and Intrusion Scope
After the intrusion, the attacker explores the network and gains access to management servers and critical systems. At this stage, vulnerabilities are exploited to expand the impact scope.
(3) Attacks on Other Servers and PCs
Attacks on other servers and devices within the network can lead to data theft or encryption, rendering the system unusable. At this stage, the damage can be extensive.
(4) Ransom Demand
Ultimately, a ransom is demanded on the condition of data recovery or prevention of information leakage. The ransom is often specified in cryptocurrencies such as Bitcoin, which have high anonymity and are difficult to trace.
Ransomware causes significant damage through sophisticated infection pathways and multi-stage attack processes. Understanding these flows and addressing system vulnerabilities is the first step in defense.
3. Ransomware Threats - 4 Risks Companies Face -
What specific damages do the threats of ransomware refer to? Here, we introduce four major risks caused by ransomware.
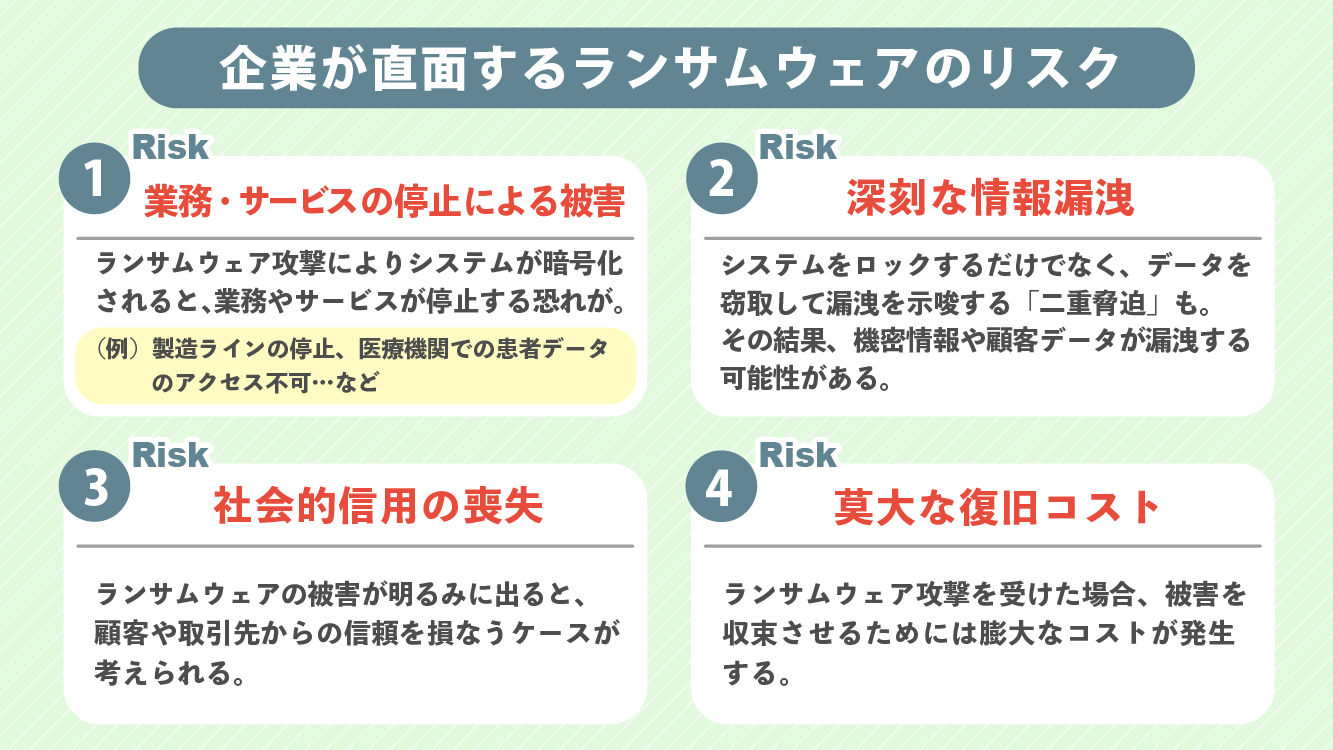
Risk.1 Damage from Business or Service Interruption
If a ransomware attack encrypts the system, there is a risk that business or services may come to a complete halt. This impact is immeasurable, especially in industries such as manufacturing, healthcare, and public services, where real-time operations are required.
▶Examples of damage: Stoppage of manufacturing lines, inability to access patient data in healthcare institutions... and more
Risk.2 Serious Information Leakage
Attackers may not only lock the system but also engage in "double extortion" by stealing data and suggesting a leak. In the event that confidential information or customer data is leaked, there is a possibility of legal action and liability for compensation to the victims.
Risk.3
When the damage from ransomware comes to light, there is a risk of losing trust from customers and business partners. Restoring trust requires a long period and significant costs, which may negatively impact performance.
Risk.4 Enormous Recovery Costs
In the event of a ransomware attack, enormous costs will be incurred to mitigate the damage.
Directly, this includes technical costs associated with data recovery and system reconstruction, and indirectly, costs related to strengthening security measures, customer support, and legal responses.
The threat of ransomware has serious impacts not only on business operations and information leaks but also on social trust and financial stability. For companies, implementing robust security measures is essential.
4. How to Respond to Ransomware
So far, we have explained the characteristics and threats of ransomware, but what measures should be taken in practice? Here, we will introduce some actions to take when affected and preventive measures to protect companies from ransomware.
If You Are A Victim of Ransomware
・Calm and prompt response
To prevent the escalation of damage and to resolve the situation with minimal impact, it is essential to respond calmly and promptly as a fundamental principle.
・Avoid paying ransom and negotiating with attackers
Generally, it is considered that one should not pay ransom. There is no guarantee that paying will restore the data, and it may encourage attackers by providing funding for future attacks. Additionally, avoid negotiating with attackers and seek advice from professionals.
Example of Initial Response After Damage Discovery

(1) Understand the scope of damage and aim to minimize it
First, identify the infected systems or devices and disconnect them from the network. Then, take isolation measures such as stopping other systems or services to prevent the spread of damage.
(2) Identify the cause of the attack and block the intrusion path
Investigate the infection routes (such as phishing emails and unauthorized access) and review the firewall and access control lists. Unauthorized communications will be blocked.
(3) Do not respond to the attacker's demands and recover from backups
Instead of complying with ransom demands, the system will be restored using backup data. It is a top priority to verify the backup data for encryption and infection, ensuring safety.
(4) Reporting to Police and Specialized Agencies
While proceeding with the above measures, we will promptly report to the police and specialized agencies related to cybersecurity (such as IPA and JPCERT). Let's seek legal procedures and support for damage response as necessary.
Preventive Measures for Ransomware
Regular security measures are essential to prevent ransomware attacks.

(1) Response to Vulnerabilities
Keeping the OS and software up to date with the latest versions reduces the risk of intrusion by addressing known vulnerabilities.
(2) Implementation of Security Software
We will implement high-performance security software to prevent malware and unauthorized access in advance.
(3) Data Backup
Important data should be backed up regularly to ensure a quick recovery in case of ransomware infection. It is recommended to keep backups both in the cloud and on offline media that are disconnected from the network.
(4) Email Measures and URL Filtering
To prevent infections from phishing emails and malicious websites, we will strengthen email security and thoroughly detect suspicious attachments and links.
(5) Employee Education
We will provide training to all employees to understand the threat of ransomware and learn how to respond to suspicious emails and links. This is expected to reduce risks associated with human factors.
It is difficult to completely prevent damage from ransomware, but appropriate initial responses and preventive measures can minimize the impact. Regular backups and the implementation of the latest security measures, as well as employee education, significantly enhance a company's defense capabilities.
5. Summary
The threat of ransomware is increasing year by year, becoming a serious risk that can directly impact the survival of companies. However, just by keeping in mind the preventive measures and initial responses introduced this time, it can lead to a reduction in damage. In particular, it is key to strengthening defenses that each employee raises their security awareness on a daily basis and is able to take appropriate actions.

What is important here is the thorough implementation of information security education.
At Human Science, we provide e-learning materials that equip you with knowledge about the latest cyber attacks and criminal tactics. We also offer foundational courses that beginners can learn with confidence. With content that allows you to systematically learn practical knowledge, we will help you improve your security literacy. Please make use of it.
You can check the details of the materials on the Human Science e-learning site.
>Information Security Fundamentals Course - Ransomware
【Related Links】
>Fundamentals of Information Security Measures in Companies <Case Study Edition>
>Fundamentals of Information Security Measures in Companies