2024.09.30
2026.01.26
How to Prevent Information Leaks from Cyberattacks? Employee Training Is Also Important!

In recent years, as cyber attacks have become more sophisticated, the risk of information leakage in companies has increased to an unprecedented level. In this era where anyone can be a target regardless of the size of the company, not only technical measures but also the awareness and actions of each employee hold the key to preventing troubles.
In this blog, we will delve into the importance of employee training to protect corporate information from cyber attacks, and provide a comprehensive explanation of typical methods of cyber attacks and the best preventive measures against them.
Table of Contents
1. Causes of Information Leakage and the Current State of Cyber Attacks
2. Typical Methods and Objectives of Cyber Attacks Leading to Information Leakage
3. Corporate Responsibilities Required When Cyber Attacks Occur
4. Thorough Measures to Prevent Information Leakage Caused by Cyber Attacks
5. Methods to Prevent Information Leakage from Targeted Attacks
6. Summary
1. Causes of Information Leakage and the Current State of Cyber Attacks

As the threat of cyber attacks increases year by year, customer information and confidential data held by companies are targeted, and cases of leakage continue to occur. First, let's organize the causes of information leakage.
Causes of Information Leakage
1. Virus Infection
Virus infection refers to malware (malicious software) infiltrating a company's system to steal information or destroy the system. Viruses often spread through email attachments, websites, USB devices, and other means. Once infected, they cause information leakage in various forms, such as "ransomware," which encrypts data and demands a ransom, or "spyware," which sends data externally.
2. Unauthorized Access
Unauthorized access refers to acts where malicious individuals, either external or internal, intrude into a company's system without permission and steal data. This includes methods such as guessing or illicitly obtaining passwords and exploiting security vulnerabilities. Unauthorized access can lead to the theft of confidential or personal information and manipulation of systems, causing serious troubles and damages.
3. Human Error
Human error due to employee carelessness is also a major cause of information leakage. For example, mistakenly sending confidential information to outsiders or failing to properly manage passwords are included. In addition, inappropriate conversations in public places and mishandling of physical documents are also factors contributing to information leakage.
4. Unauthorized Removal and Theft
Information leakage can also be caused by intentional misconduct or negligence by internal personnel. Unauthorized removal refers to employees or contractors taking confidential information without permission, while theft involves cases where information on devices or paper documents is physically taken.
5. Weak System Management
Old software and unpatched systems have security holes, making them prime targets for attackers. Additionally, when using external data storage such as cloud services, insufficient management increases the risk of information leakage.
Among the main causes, virus infections and unauthorized access are included as types of cyber attacks.
According to the Metropolitan Police Department, the most common cyber attack methods identified in 2023 targeted vulnerabilities in network devices, followed by targeted email attacks. Additionally, ransomware damage has also been prominent.
Understanding these factors and implementing appropriate countermeasures is essential to prevent information leaks.
2. Typical Methods and Objectives of Cyber Attacks Leading to Information Leaks
This chapter explains the typical methods of cyber attacks that companies should pay particular attention to.
Main Types of Cyber Attacks
●Targeted Attacks
These are attacks that infiltrate malware into systems to steal data or destroy the system. Examples include viruses, worms, trojans, and ransomware. Among these, ransomware has become a particularly significant threat in recent years.
<What is Ransomware>
Ransomware is a malicious malware that encrypts files and data stored on servers or PCs, taking them "hostage," and demands ransom or money in exchange for restoring them. It was ranked number one in the "Top 10 Information Security Threats 2025" published by IPA (Information-technology Promotion Agency, Japan). Ransomware attacks consist of four stages: "① intrusion," "② internal activity," "③ attacks on other servers or PCs," and "④ ransom demand."
〈Typical Tactics of Ransomware〉
・Encrypt files, databases, and systems to make them unusable and demand ransom
・Steal data and threaten to publish the information online (double extortion), demanding ransom
・Directly contact the individuals whose personal information was stolen to threaten and demand ransom
Daily security measures are essential to prevent ransomware attacks.
If you fall victim to a ransomware attack, it is crucial to respond calmly and swiftly. Also, since there is no guarantee that data will be restored even if the ransom is paid, and the paid ransom may fund further attacks, avoid negotiating with the attackers and seek advice from experts.
●Phishing
This is a method where attackers use fake emails or websites to trick users into giving away confidential data such as passwords and credit card information. Because the appearance mimics legitimate text or screens, users are deceived into entering their information.
●DDoS (Distributed Denial of Service) Attack
This attack uses multiple computers to send a large amount of traffic (signals or data sent and received) to the target server or network, causing the service to stop. As a result, websites and online services may become unavailable.
●SQL Injection
This attack exploits vulnerabilities in websites or web applications by inserting malicious SQL code (a language used to manipulate databases) to steal or alter personal information.
●Man-in-the-Middle Attack (MITM Attack)
This is an attack that intercepts and alters data during communication. The attacker positions themselves between the communication, stealing information between the user and the service provider or inputting false information.
●Zero-Day Attack
This is an attack that exploits vulnerabilities in software or systems before they are patched. Since attackers launch the attack before the vulnerability is publicly disclosed, it can be difficult to defend against.
As you can see, there are various methods of cyber attacks.
However, many people may not be aware of the actual purposes behind these attacks. Let’s take a closer look at the main objectives of cyber attacks.
Cyber Attack Objectives
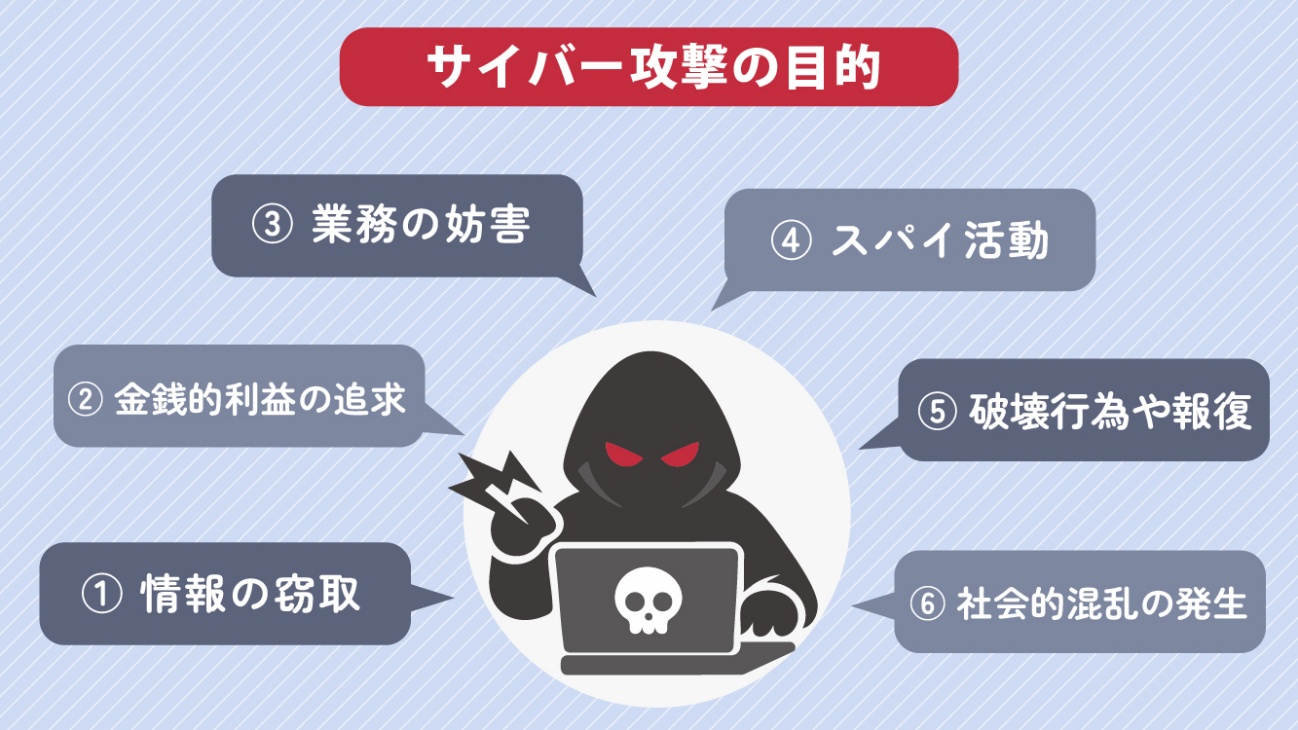
●Objective 1: Information Theft
The goal is to steal corporate confidential information and personal data. The stolen information may be sold to competitors or used for illicit purposes.
●Objective 2: Pursuit of Financial Gain
There are cases where ransomware is used to encrypt data and demand money from companies. Additionally, there are cases where attackers infiltrate the systems of banks and financial institutions to steal money directly.
●Objective 3: Disruption of Business Operations
The goal is to halt a company's operations through attacks such as Denial of Service (DoS/DDoS). This aims to cause significant financial losses to the company and damage its reputation.
●Objective 4: Espionage
The goal is to steal corporate technology and intellectual property as part of espionage activities between nations or industrial espionage. This includes attacks carried out by states or those commissioned by competitors.
●Objective 5: Destructive Acts and Retaliation
Based on political, religious, or personal motives, systems may be destroyed or information tampered with. This also includes politically motivated attacks known as hacktivism (hacker + activism).
●Objective 6: Causing Social Disorder
There are also attacks aimed at causing disruption to society and the economy. These include cyber attacks targeting critical infrastructure such as power, transportation, and communications.
Understanding the methods and objectives of cyber attacks is the first step for companies to implement effective defense measures. Continuous enhancement of security measures is required against the evolving cyber threats in the future.
3. Responsibilities of Companies When a Cyber Attack Occurs

Cyber attacks are risks that can happen to any company. What kinds of responsibilities arise for companies when damages such as information leaks or system outages occur? The following summarizes these responsibilities.
〈Corporate Responsibility in the Event of Information Leakage〉
・Responsibility for Violation of the Personal Information Protection Law
If personal information of customers or employees is leaked externally, there is a possibility of receiving guidance, recommendations, or orders from administrative authorities for failing to properly manage the data as a personal information handling business operator.
・Tort Liability and Employer Liability
Compensation claims may be made by parties who suffered damages due to information leakage. The company's management responsibility will be strictly scrutinized.
・Liability for Breach of Contract
If there is an obligation to properly manage and protect information based on a contract with a customer, but this obligation is not fulfilled, "liability for breach of contract" arises. As a result, there may be cases where the contracting party demands compensation for damages.
・Liability for Damages to Third Parties
If malice or gross negligence is recognized in the information leak, the affected parties, such as the individuals whose personal information was compromised, may claim damages.
〈Liability for Business Suspension Due to System Downtime〉
In cases where a cyber attack causes a company’s system to go down, making it temporarily difficult to continue business operations, the occurrence of damages to customers and business partners becomes a serious issue.
Especially when contractual obligations cannot be fulfilled, such as delays in product delivery or suspension of service provision, it is considered a "breach of contract," carrying risks such as liability for damages. Furthermore, if the impact of the business suspension prolongs, there is also the possibility of losing trust from customers and the public.
It is important to properly understand the required legal and social responsibilities in order to be prepared for any unforeseen circumstances.
4. Measures to Thoroughly Prevent Data Breaches Caused by Cyber Attacks

Companies that experience data breaches significantly lose trust and can sometimes incur substantial financial losses. This chapter introduces specific measures that companies should take to thoroughly prevent data breaches caused by cyber attacks.
〈Measure 1〉Implement the Latest Security Software
Security software serves as the frontline defense protecting systems from viruses and malware. Companies need to always implement the latest security software to be able to respond to new threats. Additionally, it is important to use firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) together to prevent unauthorized access to the network.
〈Measure 2〉Do Not Neglect Software Vulnerabilities
Since cyber attackers often exploit software vulnerabilities, it is important to keep software and operating systems always up to date. Updates often include security patches that fix known vulnerabilities. Additionally, utilizing vulnerability scanning tools to regularly check the network and system for vulnerabilities is also effective.
〈Measure 3〉Thoroughly Educate Employees on Security
Cyber attacks can exploit human errors and ignorance. Therefore, regular security education for employees is indispensable. It is necessary to thoroughly inform employees about basic security knowledge, such as how to identify phishing emails and how to manage passwords securely. Furthermore, regularly conducting cybersecurity training and drills helps enhance employees' response capabilities, providing greater assurance.
〈Measure 4〉Strengthen Access Control and Privilege Management
To prevent information leaks, it is also important to strictly manage access rights to confidential information. Enforce the "principle of least privilege" by granting only the minimum necessary permissions and clearly define who can access which data. Additionally, implementing two-factor authentication (2FA) or multi-factor authentication (MFA) when accessing important data helps prevent impersonation and unauthorized access.
〈Measure.5〉Thorough Data Encryption and Backup
Encrypting data is also effective in minimizing the risk of information leakage. Especially when handling confidential or personal information, encrypting data not only during transmission but also while stored prevents the content from being easily deciphered even if the data is stolen. Additionally, regularly backing up data is essential to prepare for potential data loss. It is a fundamental principle to store backups on separate devices.
〈Measure 6〉Develop an Incident Response Plan and Establish a Rapid Response System
No matter how many measures are taken, cyberattacks cannot be completely prevented. It is important to prepare for emergencies by developing an Incident Response Plan and establishing a system that can respond quickly and appropriately when an incident occurs. The plan includes step-by-step response measures such as incident detection, initial response, impact mitigation, recovery procedures, and formulation of recurrence prevention measures.
To prevent information leaks caused by cyberattacks, a multifaceted approach is necessary, including not only technical measures but also employee education and incident response planning. Furthermore, cybersecurity is not something that ends once established; continuous improvement and adaptation are required.
The key is to keep up with the latest trends while constantly enhancing defensive capabilities.
5. Methods to Prevent Information Leakage from Targeted Attacks
Among cyberattacks, targeted attacks tend to cause particularly severe damage, making it crucial for each employee to maintain vigilance and caution. This is because the emails and messages set up by attackers are crafted with great sophistication.
Here, we will provide a detailed introduction to methods for preventing information leakage caused by targeted attacks.
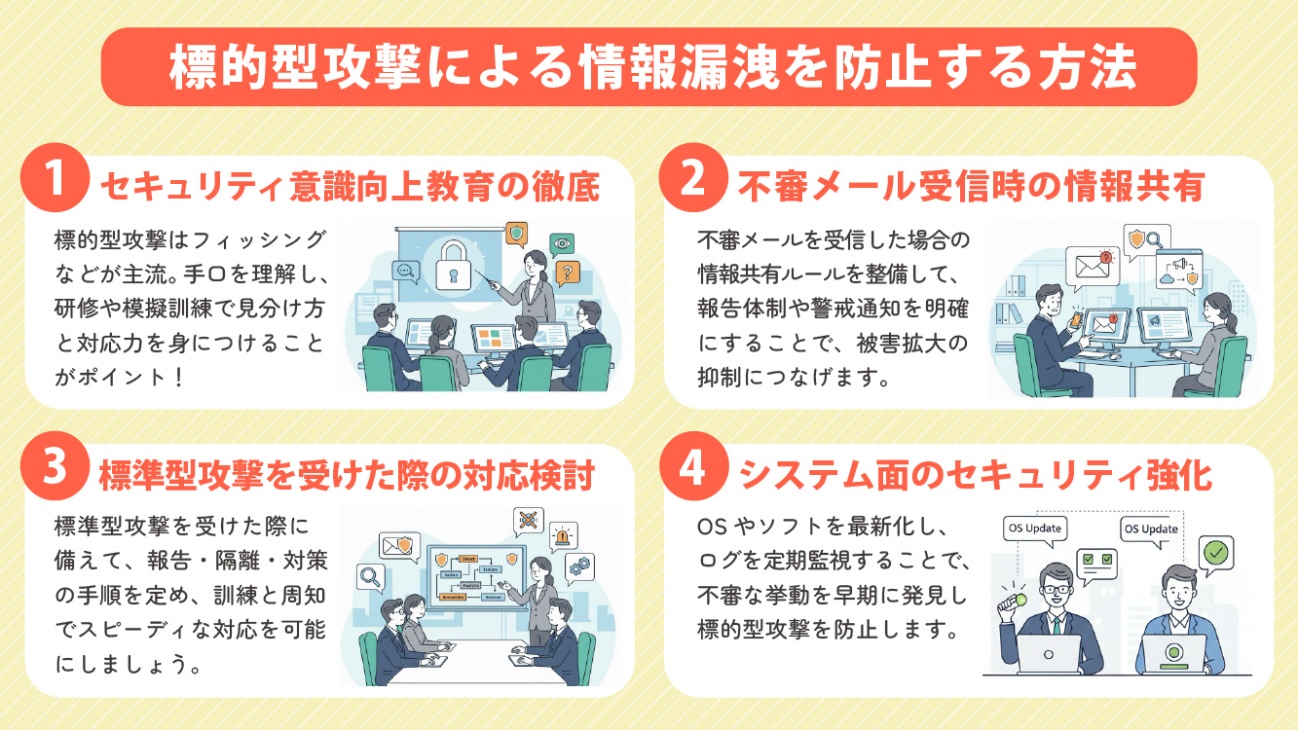
〈Method.1〉Thoroughly Implement Security Awareness Training for Employees
Many targeted attacks are carried out through phishing emails and social engineering (exploiting human psychological weaknesses or vulnerabilities to steal information). Therefore, understanding these tactics in advance is an effective preventive measure. It is advisable to provide training sessions to learn the characteristics and ways to identify phishing emails, as well as to conduct simulated exercises to develop practical response skills.
〈Method.2〉Establish Rules for Information Sharing When Receiving Suspicious Emails
By setting rules for "information sharing" in advance when suspicious emails are received, early detection of attack signs becomes possible, helping to prevent the spread of damage. The rules should include the reporting system, criteria for identifying emails, and methods for immediate alert notifications to the entire company. Strengthen the overall security of the organization through prompt information sharing and appropriate responses.
〈Method 3〉Consider Response Procedures for Targeted Attacks
By preparing in advance how to respond if an employee unknowingly opens an email involved in a targeted attack, the damage can be minimized. Specifically, this includes promptly reporting to the IT department or security personnel, conducting a system audit to determine the scope of impact, isolating devices that may be infected, and changing passwords as well as reviewing security measures. Additionally, it is important to conduct prior training and establish and disseminate guidelines so that employees can respond quickly in such situations.
〈Method.4〉Strengthening System Security
Keeping the OS and software versions up to date is one of the fundamental measures to prevent targeted attacks. Additionally, routine log checks are also important. By regularly monitoring system logs, it becomes possible to detect abnormal access or suspicious behavior early and respond promptly.
By combining these measures, a comprehensive defense system can be established, which helps minimize the risk of information leakage.
6. Summary
Cyberattacks are becoming increasingly sophisticated, posing a serious risk to corporate information assets. To prevent information leaks, it is essential to understand attack methods and have knowledge of security measures.
An effective approach is information security education utilizing e-learning.
E-learning offers the convenience of being able to study anytime and anywhere as long as there is an internet connection, and it also has the advantage of making complex security information easier to understand through illustrations and animations.
Human Science also offers a variety of teaching materials related to information security.
Among them, the "Information Security Basics Course - Targeted Attacks" provides detailed explanations ranging from knowledge about criminal methods to practical countermeasures. We also support customization for each company and multilingualization, so please feel free to contact us if you have any requests.
You can check the details of the teaching materials on the Human Science e-learning site.
>e-Learning Material "Information Security Basics Course - Targeted Attacks"