2024.04.26
Introducing common challenges and solutions for internal information security training!

In recent years, various incidents of information security, such as targeted attacks and ransomware attacks aimed at organizations and companies, as well as incidents due to non-compliance with regulations, have been reported. Specifically, these include troubles such as unauthorized access to websites, opening phishing emails, and careless handling or loss of confidential data. To prevent these damages and incidents, it is essential for all employees to acquire knowledge related to information security.
Therefore, many companies are focusing on information security training. However, there are cases where efforts are insufficient or challenges arise in education.
In this article, we will explain common challenges in information security training for employees and methods to address them. Additionally, we will introduce points to enhance the effectiveness of training.
Table of Contents
1. Background of the Importance of Information Security Education
2. Common Challenges in In-House Information Security Education
3. Solutions to Challenges in In-House Information Security Education
4. Key Points to Enhance Learning Effectiveness of Information Security Education
5. Conclusion
1. The Importance of Information Security Education

First, let's organize the background in which information security training in companies is becoming increasingly important.
1. Increase in Cyber Attacks and Rising Threats
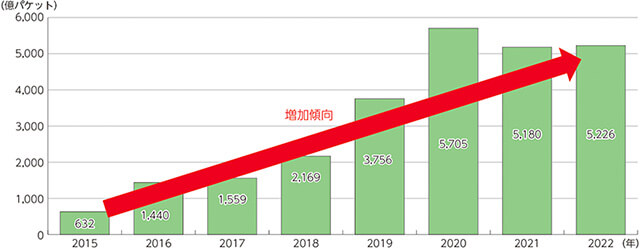
The number of cyber attacks in Japan is on the rise, and their methods are becoming more diverse and sophisticated. According to the Ministry of Internal Affairs and Communications' "Information and Communications White Paper (2023 Edition)", the large-scale cyber attack observation network operated by NICT (National Institute of Information and Communications Technology) observed approximately 522.6 billion packets of cyber attack-related communications in 2022, which is 8.3 times higher than the approximately 63.2 billion packets observed in 2015.
(Illustration) Trends in the number of communications related to cyber attacks in NICTER
2. Risk of Significant Economic Loss
The same white paper summarizes the economic losses caused by troubles related to cybersecurity, based on various organizations' research and analysis. For example, let us introduce a survey conducted by Trend Micro. In Japan, the average annual damage per organization due to security incidents that occurred in the fiscal year 2021 is estimated to be approximately 328.5 million yen.
(Illustration) Figure 4-10-2-3 Economic Losses Caused by Cybersecurity Issues
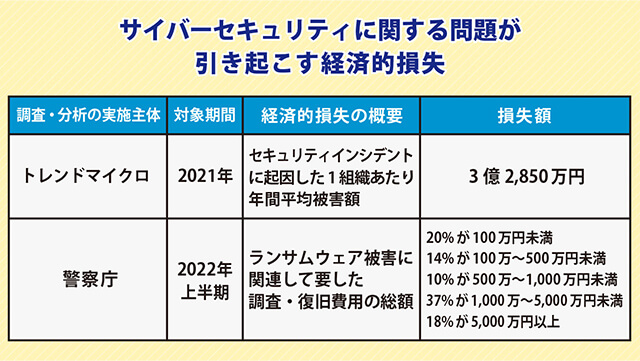
Illustration extracted from Economic losses caused by cybersecurity issues
3. Strengthening of Legal Regulations
Since the enforcement of the amended Personal Information Protection Act in April 2022, legal requirements regarding information security have become stricter in Japan. Companies and organizations are required to update their knowledge regarding information security to comply with these laws.
4. Enhancing Corporate Value and Reliability
Companies with a well-established information security management system are more likely to be trusted by customers and business partners. In other words, companies can enhance their reliability and corporate value through information security training.
5. The Need to Adapt to the Evolution of Threats
As information security threats are evolving daily, employee training must be conducted regularly based on the latest insights. Through training, we can cultivate personnel who can respond appropriately.
In this way, there are multiple factors behind the importance of information security education, all of which are crucial elements related to the survival of a company.
2. Common Issues in Internal Information Security Training

Information security training is highly important, but when trying to implement it within the company, various challenges may arise. Let's take a look at some common issues that many companies face.
Issue 1: Participants' concentration does not last
There are times when participants' concentration may wane due to monotonous content, lengthy lectures, or one-sided lecture formats. Additionally, having an internal employee serve as the instructor may lead to a lack of tension.
Issue 2: Training content lacks realism
In particular, during classroom training, it is often difficult to visualize real-life scenarios, and participants tend to proceed with their learning without a sense of reality. As a result, there is a possibility that they may not take the correct actions when a problem arises.
Issue 3: Latest trends and information are not reflected
In the field of information security, new attack methods and countermeasures are continuously being announced. Constantly reflecting this latest information in training materials can be a significant burden for companies that conduct in-house training, and it may take time to prepare and implement.
Issue 4: No perceived educational effect
If there are no follow-up or review opportunities after training, knowledge about information security may not be retained, and a sense of crisis may diminish. As a result, there tends to be a problem where the effectiveness of the education is not felt.
Issue.5 The training itself has become a mere formality
If issues like those in 1 to 4 are left unaddressed, there is a risk that participants will lose interest and engagement, turning the training into a mere routine. Additionally, participants may fail to find the purpose and significance of the training, which could lead to a decline in their motivation to learn.
To provide high-quality learning, it is necessary to be aware of such challenges and continuously review the training programs and educational materials.
3. Solutions to Issues in Internal Information Security Training

In the previous chapter, we discussed common challenges in information security training, and here we will introduce specific methods to address those challenges.
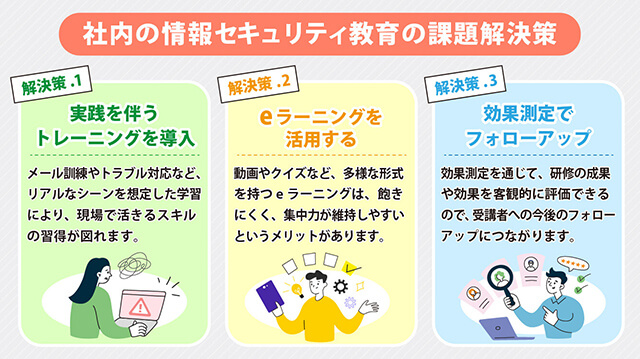
Solution to the Issue.1 Implement training that involves practical experience, such as email training
Practical training to counter targeted attacks and phishing emails is very effective. For example, in email training, participants can receive training to identify suspicious emails through a simulated experience of phishing emails. Additionally, training that simulates the response and reporting procedures within the organization, assuming a targeted attack has occurred, is also effective.
Both types of training lead to the acquisition of skills that are applicable in real-world scenarios.
Solution to the Issue.2: Utilize e-learning to provide a flexible learning environment
E-learning, a learning method utilizing the internet, provides a flexible learning environment that is not restricted by time or place. As a result, learners can choose a convenient time to engage in their studies, allowing them to efficiently absorb knowledge.
Additionally, e-learning comes in various formats such as videos and quizzes, making it easier to maintain concentration without getting bored. Furthermore, a diverse range of e-learning materials that keep up with trends are being released, making it possible to easily learn the latest information.
Solution to the Issue.3> Measure educational effectiveness and implement follow-up
After the training, it is recommended to conduct an "effectiveness assessment" to understand how well the participants have grasped the learning content. Through the effectiveness assessment, the results and impact of the training can be evaluated objectively, which also helps in improving teaching methods and materials. Additionally, it can lead to future follow-ups with the participants.
There are various measurement methods for effectiveness assessment, such as conducting tests or quizzes related to the training content to measure understanding, or having participants respond to surveys regarding the training content, evaluation of the instructor, and satisfaction with the materials.
By incorporating these solutions, various benefits such as acquiring practical skills, increasing motivation, and solidifying knowledge can be expected.
4. Key Points to Enhance the Learning Effect of Information Security Training

Solutions to the challenges of information security education also lead to improved learning outcomes. Here, in addition to the solutions introduced in the previous chapter, we will share points to further enhance learning effectiveness.
Points to Enhance Learning Effectiveness.1: Decide on the format of the training based on the participants
There are various formats for conducting training. By flexibly combining formats according to the participants' work situations, learning styles, and training objectives, effective information security education can be implemented.
Examples of Implementation Formats
■In-house Lectures
Experienced employees serve as instructors and conduct training within the company. They can provide unique and real information about the company, allowing participants to acquire practical knowledge and skills. However, since the instructor is an internal employee, it is important to maintain a sense of tension.
■Inviting External Instructors
This format involves inviting external experts and scholars to conduct seminars and lectures. As professionals, they are well-versed in the latest knowledge and trends, allowing us to obtain fresh information.
■Participate in External Training Institutions
By participating in external training institutions and seminars, learners can focus on studying in an environment away from their daily routine. They also gain opportunities to learn from the initiatives and knowledge of other companies.
■e-Learning
e-Learning, equipped with flexibility and convenience, allows learners to study according to their schedules and environments. It is also advantageous for its ease of progress management and effectiveness measurement.
Points to Enhance Learning Effectiveness.2 Choose Customizable Teaching Materials
In the field of information security, security policies and the know-how required for business differ by company and industry. Therefore, by choosing training materials that can be customized for your company, you can provide more practical learning.
Point 3 to Enhance Learning Effect: Create a System for Manualization and Information Sharing
Information security training is not only about conducting training sessions but also about creating a system for sharing information such as manuals and incident cases. By sharing the latest information and measures related to information security and accumulating know-how, employees can deepen their common understanding.
By implementing these points, it is expected that the quality of education will improve and deep learning will be promoted.
5. Summary

The frequent news of information leaks and loss incidents. These troubles not only lead to economic losses such as damages but also carry the risk of instantly collapsing the trust and image that a company has built over time. This is why strengthening security is essential for companies, and information security education holds significant importance.
In this blog, we have discussed common challenges and solutions in information security training, as well as key points to enhance learning effectiveness. As a first step, it is important to provide an environment where employees receiving training can learn enthusiastically.
Therefore, we recommend utilizing e-learning for your studies. In addition to the convenience of being able to learn anywhere as long as you have an internet connection, the wide availability of various materials related to information security is also appealing. Furthermore, ease of operation and good cost performance are additional advantages.
In Human Science, we offer e-learning services tailored to customer needs, such as the "e-Training Portal (Online Training)" where you can take e-learning courses for one month per material, and customizable "e-Training Materials Manuscript Sales".
If you are interested, please refer to the e-learning site of Human Science Co., Ltd.