2024.03.22
What are the key points for success when conducting information security training through e-learning? We will also introduce how to choose materials.

In modern society, the importance of information security is increasing. For companies and organizations to avoid risks such as information leaks and cyber attacks, it is essential for each employee to correctly understand information security and take appropriate measures.
One way to meet these needs is through the use of e-learning. However, it is essential that participants correctly understand the material and that the training is beneficial for their actual work.
Therefore, this time, I would like to explain in detail the key points for successfully conducting information security training through e-learning.
Table of Contents
1. Benefits of Information Security Training through e-Learning
2. Challenges and Solutions of Information Security Training through e-Learning
3. Examples of Content for Information Security Training through e-Learning
4. How to Choose e-Learning Materials for Information Security Training
5. Conclusion
1. Benefits of Information Security Training through e-Learning

First, what is information security training using e-learning? Additionally, I have summarized the benefits of learning information security through e-learning.
What is information security training through e-learning?
E-learning information security training is the process of educating the necessity and basic knowledge of information security measures through an online learning platform. There are various types of educational materials, including videos, simulations, quizzes, and tests, offering a diverse range of resources.
Benefits of Learning Information Security through e-Learning
Learn at your own pace, regardless of time or place
E-learning allows for learning without being constrained by time or location, as long as you have a device and an internet connection. Learners can progress at their own pace, making use of travel time and spare moments.
Review as many times as you need until you are satisfied
e-learning allows for repeated participation. For complex concepts and strategies that are difficult to grasp in one go, you can thoroughly engage in repetitive learning until you understand.
High Learning Effectiveness Expected
E-learning can utilize interactive content and simulations, so high learning effectiveness can be expected. Furthermore, it also leads to acquiring practical knowledge in information security.
Easy to Reflect Latest Information
E-learning allows for easier updates of content compared to paper-based materials such as books. Therefore, the latest knowledge and countermeasures against threats in the ever-changing field of information security can be updated immediately.
Provides low-cost and uniform education
As an advantage for administrators, e-learning is economical because it reduces costs such as printing materials, venue fees, and travel expenses for instructors and participants, unlike group training. Additionally, the same content and materials are provided to all learners, ensuring uniform education.
In this way, e-learning can be said to be an effective and flexible method of learning for information security.
2. Challenges and Solutions of Information Security Training through e-Learning
Information security training utilizing e-learning can be expected to provide effective learning, but there are also challenges. Below, we have summarized those challenges and their solutions.
In e-learning, learners need to maintain their own motivation for learning. However, if self-management skills are insufficient, there is a tendency for learning to not progress as planned, leading to a decrease in motivation.

By incorporating fun learning elements such as interactive content and gamification into educational materials, interest in learning increases, and motivation can be maintained.

Information security is a field that requires expertise, so some people struggle with the difficulty of creating e-learning materials.

It is also effective to not produce all materials in-house, but to purchase existing content or to request material production from vendors (sales companies) that provide e-learning materials. By enlisting the help of professionals with specialized knowledge, you can create high-quality materials.

In e-learning, unlike group training, it can be difficult to engage in dialogue and discussions with others, which may lead some individuals to feel isolated. As a result, there can be a decline in motivation and stagnation in learning.

By utilizing discussion forums and online chats, active interaction between learners and instructors will promote the resolution of questions and the sharing of information, leading to deeper learning.
By appropriately incorporating solutions to challenges in this way, the weaknesses of e-learning can be covered, leading to improved learning effectiveness and increased motivation.
3. Example of Information Security Training Content via e-Learning

Even though it can be said in one word that it is information security training through e-learning, in reality, there are various learning areas and a variety of materials available. In this chapter, we will introduce an example of the learning content.
Personal Information Handling and Personal Information Protection Law
Learn appropriate methods and usage for handling personal information, as well as correct disposal methods. Furthermore, deepen your understanding of the overview, purpose, and scope of the Personal Information Protection Act.
Social Media Usage Rules and Risks
Understand the company's social media usage policy and learn the behavior guidelines based on it. Specifically, this includes precautions for information dissemination both internally and externally, appropriate responses to defamation and criticism, and protective measures against unauthorized access to social media accounts, among others.
Compliance
Understand the laws and regulations that companies must comply with, and learn about their importance and impact on society. Additionally, learn about the ethical standards and codes of conduct that companies uphold, and promote actions based on those principles.
Threats and Countermeasures of Targeted Attack Emails
Learn to understand the attack methods of targeted phishing emails, such as clever disguises, links, and attachments, and how to identify suspicious emails and respond appropriately. You will also understand the response and reporting procedures upon receipt, emphasizing the importance of quick initial response.
ID and Password Management
Learn how to safely and appropriately manage IDs and passwords through knowledge of creating hard-to-guess passwords, the importance of regular changes, and how to deal with social engineering attacks aimed at stealing passwords.
Risk of Using Cloud Services
Learn about the risks that may occur when using cloud services, such as data leaks and account hacks, and acquire the knowledge and skills to use them safely.
In training, it is also effective to cover case studies of incidents along with this kind of knowledge. By encountering real-life incident case studies, learners can feel the problems and risks more vividly, fostering a sense of urgency. As a result, their understanding of information security deepens, leading to the acquisition of appropriate countermeasures and preventive measures.
4. How to Choose e-Learning Materials for Information Security Training
Choosing the right materials is also important for successfully conducting information security training using e-learning. Here are some key points to keep in mind when selecting materials.
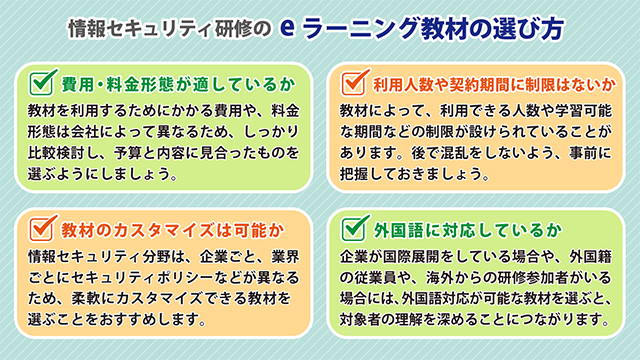
Is the cost and pricing structure appropriate?
The costs associated with using educational materials vary by the company providing them. Additionally, the pricing structures are diverse, ranging from free options to one-time purchase models with only initial costs, subscription models with monthly fees, and pay-per-use options that incur charges each time the materials are used. When implementing, be sure to compare each educational material and choose one that fits your budget and content needs.
Are there any restrictions on the number of users or the contract period?
Some materials may have restrictions on the number of users and the duration of study. By understanding the number of participants and the usage period in advance, you can prevent confusion and avoid unnecessary expenses.
Can the teaching materials be customized?
Teaching materials can be divided into those that are used as provided by the supplying company and those that are customized for in-house use. In the field of information security, security policies and the know-how required for business vary by company and industry, so it is recommended to choose teaching materials that can be flexibly customized.
Is it compatible with foreign languages?
When a company is expanding internationally or has foreign employees or training participants from abroad, it is important to choose materials that are available in foreign languages. Learning in one's native language can deepen understanding and improve learning effectiveness.
We recommend selecting materials that match the training objectives and the needs of the participants while considering these points.
5. Summary

To deepen the understanding of the constantly changing field of information security, it is essential to have up-to-date materials that reflect the latest information and a flexible learning environment. E-learning equipped with these elements can be considered the optimal learning tool.
To maximize the learning effectiveness of e-learning, the "quality of the materials" is important.
As explained in this blog, there are various types of materials and different ways to use them. Some materials are available for free trials, so actively utilize them to assess their usability, cost performance, and whether they meet your company's needs, and choose carefully.
Human sciences also offer a wide range of educational materials related to information security.
We incorporate essential knowledge on various themes, such as those focused on devices like computers and smartphones, as well as those specialized for telework and remote work, and we also include interactive elements like quizzes for verification.
We also offer a free trial, so if you are considering it, please feel free to give it a try.
Please refer to the e-learning site of Human Science Co., Ltd.